Ransomware (CryptoLocker, CryptoWall, TeslaCrypt etc): What it is and what you can do about it
Ransomware isn’t a new topic but new variants seem to emerge on a pretty regular basis but we’re still seeing quite a high rate of occurrence at the moment so this seems to be a good time for a post on the subject.
What is ransomware or crypto malware anyway?
Ransomware is a type of computer virus which you can ‘catch’ in a number of ways, most typically the infection spreads via email attachments which contain ordinary looking files which actually contain a trojan which then runs a hidden programme on your computer. This programme will then (very quickly) encrypt certain files that it finds on your computer (and your servers or NAS devices if those are mapped via network drives). Once this process completes, your documents are then totally unreadable until the process is reversed.
The virus writers demand a “ransom” – usually to the tune of about 300 USD to be paid (in bitcoin, which keeps the payment untraceable) – in order to reverse the encryption so that you can access your files again.
It may seem silly that they expect you to hand over money to an unscrupulous hacker – and it’s certainly not something we recommend doing (you’re basically financing cyber-crime) – but it is worth noting that these guys aren’t doing this for the thrill; this is a commercial operation, and getting paid to reverse the encryption is a key part of their business model. They need to ensure that they have enough of a ‘trusted reputation’ in the market to get paid by a high number of victims.
The entire process can take up to a couple of days from first detection until you’re back up and running (this depends on various factors such as how much data you have and how long it takes to acquire bitcoin and make the payment etc). So, in addition to the outright expense of paying the ransom – and potential IT costs on incident response, victims of this sort of attack also experience a couple of days of downtime whilst bitcoin is purchased, ransom is paid, files are decrypted etc.
What can you do?
Prevention is much better than cure. That said, the best cure is to be able to restore from a backup. Backups are a non-optional, no-brainer, insert-other-obvious-phrase-here must-have. So backup, backup, backup, backup, backup. Yes, I said that five times. I’ll explain why later in this post.
Before that though, let’s talk about prevention.
- Ensure up to date & effective anti-malware across the network (this means on the endpoints, your desktops, laptops, servers) – but do be aware that this does not guarantee safety, as most AV vendors use signatures – and all an attacker needs to do is change a small amount of code in the malware to avoid detection. A good AV product will catch all “known variants” but will not be able to combat zero-day malware. Note that we use the term AV (anti-virus) as a generic term but you want to ensure you run a sophisticated anti-malware solution (or solutions) that looks for all sorts of malware, including virus, spyware, phish, trojan etc. Two products that we really like in the SME space are Webroot and MalwareBytes AntiMalware. If you have a requirements and budgets that are above normal, there are other products that we work with such as Bit9 + Carbon Black that provide more sophisticated threat detection, prevention, containment & response capabilities. We work with each of these products ourselves and stand behind this recommendation.
- Ensure that you have a robust email security system in place – but be aware that this does not guarantee safety, as most AV vendors use signatures – and all an attacker needs to do is change a small amount of code in the malware to avoid detection. Email security systems will catch all “known variants” but will not be able to combat zero-day malware. It is worth noting that in most cases a ‘good’ email security system is in the cloud, and catches lots of bad stuff well before it makes it to your network or servers.
- Ensure users do not have administrative access to their machines. If a user can’t run a programme as administrator, this greatly reduces the attack surface. This is such an easy thing to do, and yet we see so many organisations completely ignoring this very basic principle of least privilege. Sadly, some application vendors ship out badly written software that require elevation to run but in a lot of cases its just down to laziness – lock down your systems!!
- Ensure that your backups are current, tested, accessible and quick to restore. We know from direct experience that even if backups exist there may be a temptation will be to pay the ransom if the backups are too slow, unreliable or cumbersome.
- Use a reliable web content filtering system to prevent access to ‘dodgy’ sites but be aware that frequently ‘non-dodgy’ sites can be compromised and spread malware without the site owners even knowing.
- Ensure that all your devices are kept fully up to date with the latest patches and security updates from all vendors – in most cases this is Microsoft updates, but it is also important to ensure you patch 3rd-party applications such as those provided by Adobe, Java etc.
Below are a couple more technical but very useful measures – these designed to be read and implemented by experienced network administrators. Click here to skip the tech bits.
Configure your perimeter firewall to block access to Tor.
Why Tor? Because typically a lot of the communication to the hacker’s remote (C&C) servers occurs over Tor. So – no Tor, no comms, no exploit. The exact steps to achieve this depend on the perimeter firewall you operate but by way of example, here is how you would easily achieve this using a fairly popular SME firewall appliance called a SonicWALL.
Log into the admin console, and locate the Application Control section under Security Services:
Enable App Control:
Ensure that the database is up to date:
Use the drop-down filters to find Category: Proxy-Access, Application: Tor, edit and block it:
Finally, ensure that you have enabled App Control on the relevant zones:
Congratulations – you’ve now blocked Tor, and taken a big step forward in securing your network already!
Configure your network policies to prevent execution of files from the AppData folder.
This section applies to those organisations that run Windows based Active Directory networks. The notes below contain very brief instructions on how to lock down your Windows Active Directory network to prevent execution of certain types of applications from certain locations on a computer. Whilst nothing is 100%, this approach will greatly improve the security of your network against not just crypto / ransomware but all sorts of unsanctioned programmes.
Warning: These changes should only be carried out by an experienced system administrator after thorough testing. On most sites these settings will need further tweaking and if you roll out without testing you could render your client computers useless until rolled back. And you will definitely not win Employee of the Month or any popularity prizes.
Typically, create a new GPO and proceed as follows:
We start by defining a new Software Restriction Policy (SRP):
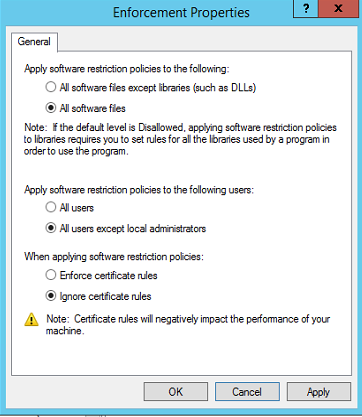
Let’s choose our enforcement settings:
Next, we create something called a path rule – this basically defines a specific file system path and then a rule to apply to that path:
So it’s as easy as selecting a path and choosing a security level:
You will then want to create a number of such path rules until your draft policy looks something like:
At this stage you have now created new SRP which will prevent users from running executables in the paths defined by your policy.
We can then go a step further and define another setting that prevents users spawning Windows Script Host processes which can then be used to download more malware. We do this by creating 2 new registry items (one each for HKLM and HKCU) and pushing them out via GPP:
The paths above are
SOFTWARE\Microsoft\Windows Script Host\Settings
That’s it!
So we’ve now also locked down our Windows system to prevent not just ransomware from running but also loads of other potential baddies or just unauthorised applications that users may end up running – intentionally or otherwise.
It is important that you test these settings thoroughly on your network before rolling out. Consider a staggered rollout depending on the size and complexity of your environment and also communicate with your users so that they know to expect some changes. Any users who are sticking to their approved applications and doing nothing beyond that should notice no difference at all.
People Measures:
Ensure that all staff undergo at least basic security awareness training so that they are aware of the following:
- Never open email attachments from unknown senders, and only open attachments from known senders if they are quite certain of their legitimacy. It is perfectly acceptable to reply to an email and ask a sender if they meant to send an attachment.
- To restrict their web browsing to legitimate business-related sites (use technical measures to enforce this)
- Never download files from websites unless they are certain of their validity – remind them that even legitimate websites can be compromised.
- Remind them of the consequences to the business of their failure to comply with security guidance & policy
- Have an appropriate security policy in place that details what the individual consequences are of failing to comply with security guidance & policy
What to do if you have already been attacked:
- Find the source of the infection, isolate and clean up that computer
- Restore data from backup
- As a last resort – pay the ransom, but beware that you are effectively funding cyber-terrorism & extortion.
- Start at ‘Prevention’
Have a backup! (aka: What is an effective backup strategy?)
Although the right choice of backup strategy varies from case to case and depends on a range of factors including (but not limited to) your specific RPO & RTO, there are some basics that are common to most of us:
- Shadow copies: If you’re like a lot of us, you have Windows servers providing file storage services to your network. The first and easiest way to have a copy of backups is to enable shadow copies. This is usually an extremely quick, painless & FREE method of having a readily-available backup version of files that you can roll back to at the click of a button. As long as your file server isn’t the source of the attack, this method alone could allow you to fully recover from a ransomware attack.
- Local backups: Have a separate copy of file data (and all your other data for that matter) sitting in a different location on your network. This protects against loss (hardware, software or malware-related) of whatever system hosts your live data.
- Offsite backups: Ensure that you have a copy of your data offsite. Ideally this will be a zero-touch, automated, encrypted backup that is reported on daily and tested routinely.
- Rotation schemes: For most business you will want a backup rotation scheme such as grandfather-father-son which keeps separate copies of daily, weekly & monthly backups. In many cases we also keep quarterly and annual copies of data. Some types of data is only accessed once a year and we protect against any loss of that information by keeping a copy of those data sets for 1 year + 1 month.
- Disaster Recovery: Consider the consequences of a total failure of your site. What will happen to business if your office is no longer usable? There are numerous possible scenarios – fire, flood or even just severe weather that prevents staff from getting to work. Will the business be able to continue functioning and serving customers? If not, what are the consequences of that? What are your critical services? How quickly can these be re-established? Will you be able to communicate with your staff, suppliers & customers? These are but a few of the most basic questions to consider when thinking about a DR / BC (business continuity) plan.
A lot of organisations we talk to haven’t really thought about a disaster recovery or business continuity plan. So if you’re in the same position – don’t worry, you’re not alone! The important thing is to have a plan. Even if you don’t end up investing in spinning up a cloud DR/BC site – at least you will have had a chance to think through some of these processes, so if the unexpected does happen you’ve already got a plan in place which you can start executing rather than panicking!
So – that’s it for now, do let us know what you think by leaving a comment below – and feel free to shout if you’re looking at this and scratching your head – that’s what we’re here for.